Unleashing Advanced Penetration Testing Solutions
In the ever-evolving realm of cybersecurity, securing your organization’s digital assets requires a multifaceted approach. While traditional penetration testing provides a valuable foundation for identifying vulnerabilities, advanced penetration testing delves deeper, employing sophisticated techniques to simulate real-world attack scenarios with greater complexity and realism.
Imagine advanced penetration testing as a highly-skilled red team tasked with finding every possible chink in your organization’s cyber defenses. Their relentless pursuit of vulnerabilities mirrors the strategies employed by real-world attackers, ultimately providing you with a deeper understanding of your security posture and the areas requiring further hardening.
In the following sections, we’ll delve deeper into the specific techniques and benefits of advanced penetration testing, highlighting how it can significantly enhance your organization’s overall cybersecurity effectiveness.
Table of Contents
Understanding Advanced Penetration Testing Methods
Traditional penetration testing plays a crucial role in identifying vulnerabilities, but advanced testing takes security assessment to the next level. Here, we explore some of the sophisticated techniques employed by advanced penetration testers:
1. Social Engineering
- Beyond technical exploits: Advanced testers understand that human vulnerabilities can be just as exploitable as technical ones. They may employ social engineering tactics, such as phishing emails, phone calls, or impersonation, to trick employees into revealing sensitive information or granting unauthorized access.
2. Custom Malware Development
- Evolving past known threats: Traditional testing often focuses on known vulnerabilities and readily available exploit kits. Advanced testers, however, may go a step further, developing custom malware specifically tailored to exploit unique vulnerabilities identified during the testing process.
3. Internal Network Exploitation
- Moving beyond the perimeter: Traditional testing often focuses on external attack vectors. Advanced testing, however, delves deeper, simulating how attackers might move laterally within your network after gaining an initial foothold. This involves exploiting vulnerabilities in internal systems and escalating privileges to gain access to critical data or resources.
4. Cloud Security Assessments
- Securing the modern landscape: As businesses increasingly rely on cloud-based infrastructure, advanced testing needs to adapt. Testers possess expertise in assessing the security of cloud environments, identifying potential vulnerabilities in cloud configurations, data storage practices, and access controls.
5. Wireless Network Penetration Testing
- Securing all entry points: Advanced testing extends beyond traditional wired networks, assessing the security of wireless access points. This involves identifying vulnerabilities in Wi-Fi configurations, testing for weaknesses in encryption protocols, and attempting unauthorized access through various techniques.
6. Physical Security Assessments
- Addressing the human element: While often overlooked, physical security plays a crucial role in overall cybersecurity. Advanced testing may involve physical assessments of your facilities, looking for vulnerabilities such as weak access controls, tailgating opportunities, or unsecured devices that attackers could exploit.
7. Zero-Day Exploit Research
- Staying ahead of the curve: Advanced penetration testers may even engage in zero-day exploit research, attempting to discover previously unknown vulnerabilities in software or hardware. This allows organizations to proactively address potential threats before they are exploited by malicious actors.
By employing these sophisticated techniques, advanced penetration testing goes beyond the limitations of traditional approaches, offering a more comprehensive and realistic assessment of your organization’s security posture. This deeper understanding empowers you to identify and address even the most complex vulnerabilities, ultimately fortifying your defenses against evolving cyber threats.
Benefits of Advanced Penetration Testing
By employing sophisticated techniques, it offers a range of significant benefits:
1. Enhanced Threat Detection
- Advanced penetration testing employs sophisticated techniques and methodologies to enhance threat detection capabilities. By mimicking real-world attack scenarios and leveraging cutting-edge tools, testers can identify and mitigate advanced threats that traditional testing methods may overlook.
- By proactively identifying and addressing advanced threats, organizations can effectively mitigate cybersecurity risks and prevent potential security breaches.
2. Comprehensive Vulnerability Assessment
- Advanced penetration testing provides a comprehensive assessment of vulnerabilities across an organization’s infrastructure. Through in-depth analysis and exploitation of complex vulnerabilities, testers can identify and prioritize critical security weaknesses that pose the greatest risk to the organization.
- By prioritizing critical vulnerabilities, organizations can allocate resources more effectively to remediate high-impact security issues, thereby strengthening their overall security posture.
3. Proactive Security Measures
- Advanced penetration testing enables organizations to take proactive security measures to defend against evolving cyber threats. By simulating advanced attack scenarios and identifying potential security gaps, organizations can implement proactive security measures to mitigate risks and prevent potential security breaches.
- By adopting proactive security measures based on the findings of advanced penetration testing, organizations can enhance their resilience to cyber threats and better protect their sensitive data and assets.
Through these benefits, advanced penetration testing plays a crucial role in helping organizations stay ahead of emerging cyber threats, strengthen their security defenses, and safeguard their digital assets against sophisticated adversaries.
Advanced Penetration Testing Solutions: Elevating Your Cybersecurity Defenses
At Pillar Support, we offer advanced penetration testing services in collaboration with our trusted partner, Vonahi Security. Our cutting-edge solutions leverage advanced techniques to provide comprehensive network protection and safeguard your organization against evolving cyber threats.
Why Choose Us
- Expertise in Advanced Techniques: Our team of cybersecurity experts is proficient in employing advanced penetration testing methodologies and tools to uncover complex vulnerabilities that traditional approaches may miss. We utilize state-of-the-art techniques to simulate real-world attack scenarios and identify potential security gaps within your infrastructure.
- Tailored Solutions: We understand that every organization has unique cybersecurity challenges. That’s why we offer tailored penetration testing solutions that are customized to meet your specific needs and address your organization’s most critical security concerns. Whether you operate in a highly regulated industry or have complex network architectures, we have the expertise to provide targeted testing solutions tailored to your environment.
- Comprehensive Network Protection: With our advanced penetration testing services, you can benefit from comprehensive network protection that goes beyond surface-level assessments. We conduct thorough vulnerability assessments and prioritize critical security weaknesses to help you strengthen your overall security posture and mitigate cyber risks effectively.
Partner with us to enhance your organization’s resilience to cyber threats and ensure the integrity of your digital assets.
Take Your Cybersecurity to the Next Level
Don’t leave your valuable assets vulnerable. Schedule a consultation with our team today to discuss your specific security needs and explore how our advanced testing services can help you:
Dial 212-255-3970 and ask for Michael or Richard to discuss a PenTest solution tailored to your company’s needs.
Frequently Asked Questions
What is Advanced Penetration Testing?
Advanced penetration testing refers to a sophisticated approach to testing the security of an organization’s systems, networks, and applications. It involves using advanced techniques and methodologies to identify vulnerabilities that may not be detected by traditional testing methods. Advanced penetration testing goes beyond basic vulnerability scanning and involves simulating real-world attack scenarios to assess the effectiveness of an organization’s security controls.
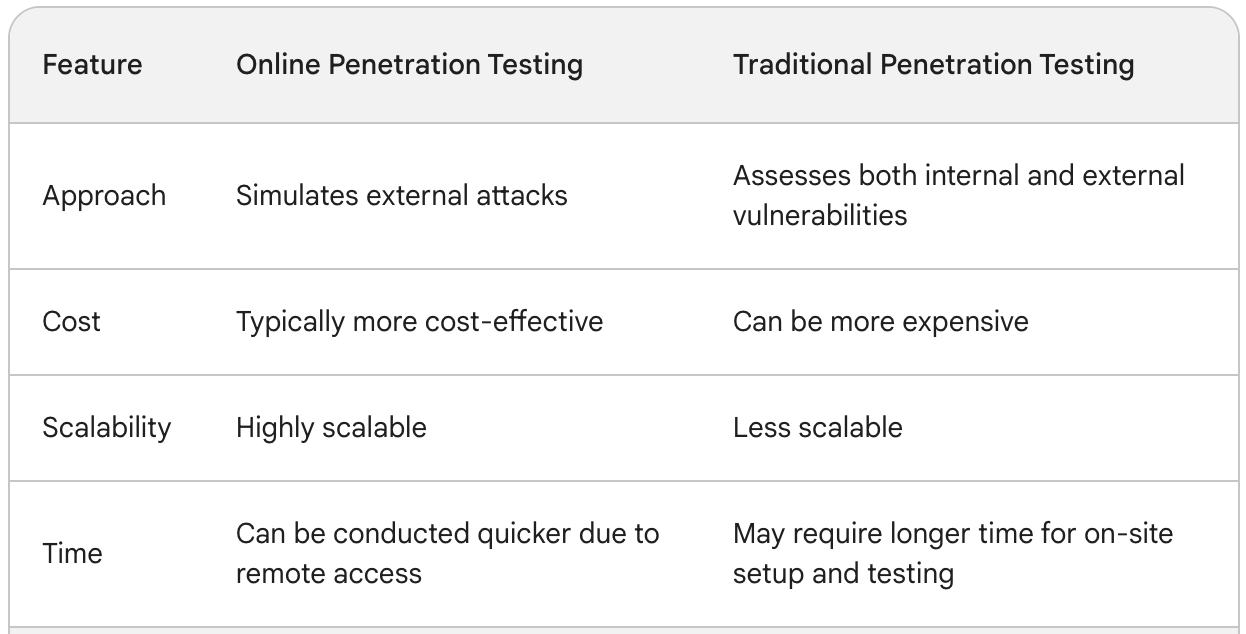
How Does Advanced Penetration Testing Differ from Traditional Methods?
Advanced penetration testing differs from traditional methods in several key aspects:
1. Complexity: Advanced penetration testing utilizes more complex techniques and methodologies compared to traditional methods, which may involve basic vulnerability scanning and testing.
2. Scope: Advanced penetration testing typically has a broader scope, covering a wider range of systems, networks, and applications within an organization.
3. Real-world scenarios: Advanced penetration testing simulates real-world attack scenarios, such as targeted attacks or sophisticated cyber threats, to assess an organization’s resilience to such threats.
4. Depth of analysis: Advanced penetration testing involves a deeper analysis of vulnerabilities, often uncovering more subtle or complex security weaknesses that traditional methods may overlook.
5. Customization: Advanced penetration testing can be tailored to the specific needs and risk profile of an organization, whereas traditional methods may offer more standardized testing approaches.