Exploring Online Penetration Testing Solutions

In the ever-expanding digital world, securing online assets and infrastructure is paramount. Online penetration testing emerges as a vital tool in today’s cybersecurity landscape, empowering businesses to identify and address vulnerabilities within their web applications, websites, and other internet-facing systems.
Table of Contents
What is Online Penetration Testing?
Online penetration testing, also known as web application penetration testing, simulates real-world attacks launched from the internet. By employing various techniques and tools, ethical hackers, or security professionals, attempt to exploit security weaknesses in your online systems. This proactive approach helps you discover vulnerabilities before malicious actors can, allowing you to address them and strengthen your digital defenses.
Why is Online Penetration Testing Important?
Online penetration testing offers a comprehensive solution, providing numerous advantages for organizations seeking to proactively bolster their cybersecurity posture.
Key Advantages of Online Penetration Testing
1. Convenience and Accessibility
- Online testing eliminates the need for on-site visits from security professionals, reducing logistical complexities and streamlining the testing process.
- Testing can be scheduled and conducted remotely, offering greater flexibility and accommodating diverse time zones and organizational needs.
2. Scalability and Cost-Effectiveness
- Online testing solutions can be tailored to the specific needs and budget of your organization, making them a scalable and cost-effective option for businesses of all sizes.
- Automated testing tools can efficiently scan large volumes of data and code, saving time and resources compared to manual testing methods.
3. Real-Time Insights and Reporting
- Online testing often provides real-time results and comprehensive reports, enabling you to quickly identify vulnerabilities and prioritize remediation efforts.
- Detailed reports usually include the severity of vulnerabilities, potential impact, and recommended mitigation strategies, offering actionable insights for immediate action.
4. Continuous Monitoring and Vulnerability Management
- Some online testing solutions offer ongoing monitoring capabilities, allowing you to identify and address emerging threats promptly.
- This proactive approach to vulnerability management can significantly reduce the risk of successful cyberattacks and data breaches.
5. Expertise and Industry Knowledge
- Many online testing providers employ highly skilled and experienced penetration testers who stay updated on the latest threats and vulnerabilities.
- This expertise ensures your organization benefits from the latest knowledge and techniques in the ever-evolving cybersecurity landscape.
By opting for online penetration testing solutions, you gain access to a convenient, scalable, and cost-effective approach to securing your online assets. Real-time insights, continuous monitoring, and access to expert knowledge empower you to proactively identify and address vulnerabilities, ultimately strengthening your online security posture and minimizing the risk of cyberattacks.
Understanding the Online Penetration Testing Process
Let’s delve into the step-by-step process of online penetration testing:
- Scoping: The first step in the online penetration testing process involves defining the scope of the assessment. This includes identifying the systems, applications, and network segments to be tested, as well as specifying the testing objectives and goals.
- Reconnaissance: The reconnaissance phase involves gathering information about the target systems and network infrastructure. This may include identifying IP addresses, domain names, network services, and potential vulnerabilities through passive information-gathering techniques such as OSINT (Open Source Intelligence) and active scanning methods like port scanning.
- Vulnerability Assessment: During this phase, automated vulnerability scanning tools identify known security vulnerabilities and misconfigurations in the target systems and applications. Vulnerability scanners perform comprehensive scans of the target environment, including web applications, network devices, and databases, to detect weaknesses that attackers could exploit.
- Exploitation: In the exploitation phase, penetration testers attempt to exploit identified vulnerabilities to gain unauthorized access to the target systems or sensitive data. This may involve launching targeted attacks, such as SQL injection, cross-site scripting (XSS), or remote code execution, to demonstrate the potential impact of the vulnerabilities and validate their severity.
- Post-Exploitation: Once access has been gained to the target systems, penetration testers conduct post-exploitation activities to further assess the security posture of the environment. This may include escalating privileges, pivoting to other systems, and exfiltrating sensitive data to simulate real-world attack scenarios and assess the effectiveness of security controls.
- Reporting: The final phase of the online penetration testing process involves documenting and reporting the findings of the assessment. A detailed report is prepared, outlining the vulnerabilities discovered, their severity levels, and recommendations for remediation. The report may also include evidence of successful exploitation, screenshots, and technical details to assist stakeholders in understanding the risks and prioritizing mitigation efforts.
Throughout the online penetration testing process, various tools, techniques, and methodologies are utilized to simulate cyber-attacks, identify weaknesses, and assess the effectiveness of security defenses. By following a structured and systematic approach, organizations can enhance their cybersecurity posture, mitigate risks, and safeguard their digital assets against potential threats.
Key Considerations When Choosing an Online Testing Provider
With numerous providers offering various services, selecting the most suitable partner requires careful consideration of several key factors.
Here are some essential factors to ponder when choosing an online penetration testing provider:
- Expertise and Experience: Opt for a provider with a qualified team and a successful track record.
- Methodologies and Tools: Ensure they use industry-standard testing techniques and tools.
- Customization and Flexibility: Look for tailored solutions to meet your unique needs.
- Reporting and Documentation: Seek detailed reports with actionable insights and ongoing support.
- Compliance and Accreditation: Verify adherence to industry standards and relevant certifications.
- Reputation and References: Research client feedback and seek references to gauge satisfaction.
- Cost and Value: Balance pricing with the quality and effectiveness of their services.
Prioritizing these considerations will help you select a provider that aligns with your cybersecurity requirements and delivers reliable testing solutions.
Online Penetration Testing vs. Traditional Testing Methods
Key Differences
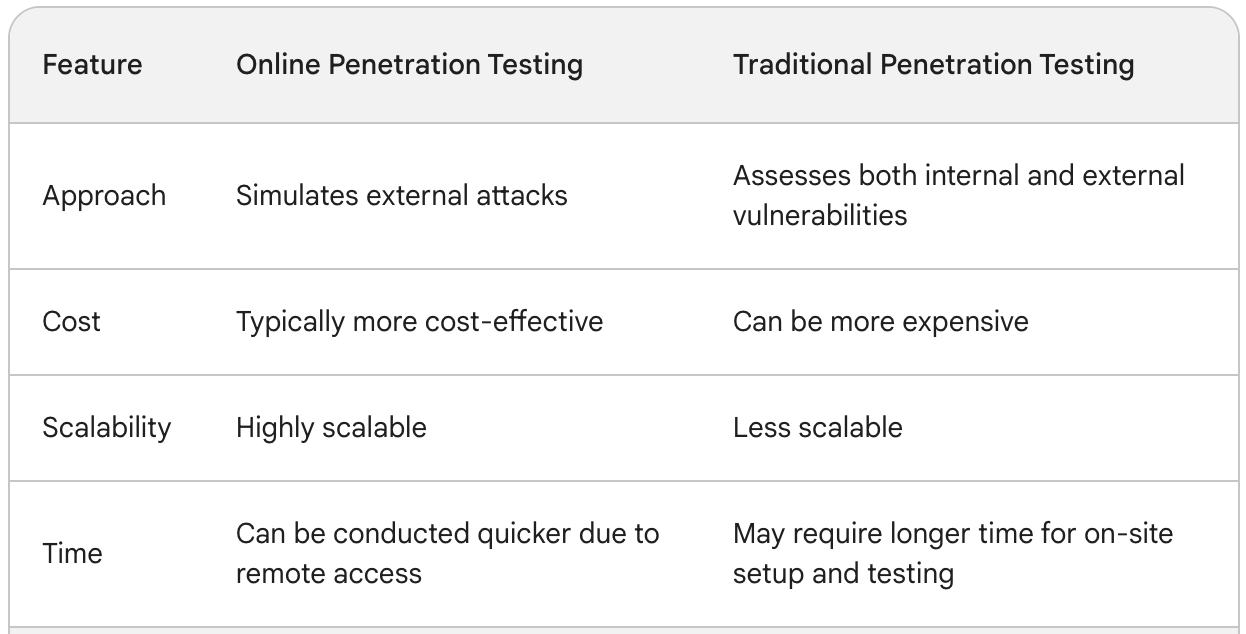
Choosing the Right Method
- Online testing: Best suited for evaluating the security of web applications, APIs, and other internet-facing systems. It’s also an efficient option for organizations with limited budgets or tight schedules.
- Traditional testing: Ideal for comprehensive security assessments encompassing your entire IT infrastructure, including internal systems, network devices, and user workstations. This method is preferred for organizations with strict compliance requirements or those managing highly sensitive data.
Both online and traditional penetration testing offers valuable tools for securing your organization’s digital assets. Selecting the most appropriate method hinges on your specific needs, considering factors like budget, scalability, and the scope of the security assessment required.
Common Challenges and Solutions
While online penetration testing offers numerous advantages, it also presents certain challenges that need to be addressed to ensure a successful and comprehensive assessment. Here are some common challenges and how to overcome them:
Challenge 1: Limited Visibility
Unlike traditional on-premise testing, online testing often lacks complete visibility into the internal workings of an application or system. This can make it difficult to identify vulnerabilities that reside within the application logic or server-side components.
Solution:
- Combine online testing with code review: Conduct a code review alongside online testing to gain a deeper understanding of potential vulnerabilities within the application code.
- Leverage API testing tools: Utilize specialized tools to test the security of APIs that connect the web application to backend systems.
- Request additional access (if feasible): In certain cases, with proper authorization and justification, requesting limited access to specific internal systems might be an option to gain deeper insights.
Challenge 2: False Positives
Automated vulnerability scanners often generate false positives, indicating vulnerabilities that are not exploitable in reality. This can lead to wasted time and resources investigating non-existent threats.
Solution:
- Manual verification: Employ skilled testers to manually verify the findings of automated scanners, focusing on the most critical and likely vulnerabilities.
- Utilize advanced scanning tools: Invest in advanced scanning tools that offer better accuracy and reduce the likelihood of false positives.
- Prioritize based on context: Analyze identified vulnerabilities in the context of your application and infrastructure, prioritizing those with the highest potential impact.
Challenge 3: Scope Creep
The initial scope of the testing engagement might not encompass all critical aspects of the online environment. This can lead to incomplete assessments and leave certain vulnerabilities undiscovered.
Solution:
- Thorough planning and scoping: Clearly define the scope of the testing engagement through collaboration with the testing provider, considering all critical systems and functionalities.
- Phased approach: Consider a phased testing approach, starting with core functionalities and expanding the scope based on initial findings and risk assessment.
- Maintain open communication: Maintain open communication with the testing provider throughout the engagement to discuss potential adjustments to the scope based on emerging findings.
Challenge 4: Limited Time and Budget
Budgetary constraints and tight timelines can limit the comprehensiveness of the testing engagement.
Solution:
- Prioritize testing based on risk: Focus testing efforts on the most critical applications and functionalities that pose the highest risk to your organization.
- Leverage automated tools: Utilize automated scanning tools to efficiently identify common vulnerabilities, freeing up time for manual testing of complex areas.
- Phased approach: Consider a phased testing approach, allocating resources strategically to address critical areas first and potentially expanding the scope later.
By understanding these common challenges and implementing the suggested solutions, you can enhance the effectiveness of your online penetration testing and gain valuable insights into the security posture of your online assets.
Online Penetration Testing: Securing Your Digital Assets
Looking to fortify your online defenses against cyber threats? Partner with us, Pillar Support, in collaboration with Vonahi Security, a leader in cybersecurity solutions. Our comprehensive online penetration testing services are designed to identify and mitigate digital vulnerabilities, ensuring robust protection for your digital assets. Call 212-255-3970 and ask for Michael or Richard to discuss a PenTest solution tailored to your company’s needs.
Frequently Asked Questions
Can I Do My Own Penetration Testing?
While it’s technically possible for individuals to conduct their own penetration testing, it’s generally recommended to hire professional cybersecurity firms with expertise in this area. DIY testing may lack the depth, accuracy, and comprehensive analysis provided by professional services.
How Does Online Penetration Testing Differ from Traditional Methods?
Online penetration testing differs from traditional methods primarily in the approach and delivery. Traditional methods often involve on-premises assessments conducted by physical presence, while online testing is performed remotely over the internet. Online testing offers greater accessibility, scalability, and efficiency compared to traditional methods.